Grandpa
Target IP: 10.129.95.233
Attacker IP: 10.10.14.11
1. 정보수집
nmap
결과 > 80번 포트만 오픈됨.
$ nmap -sV -sC --open -Pn -n --max-retries 2 --min-rate 6000 10.129.95.233 -oA svsc
>
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
| http-methods:
|_ Potentially risky methods: TRACE COPY PROPFIND SEARCH LOCK UNLOCK DELETE PUT MOVE MKCOL PROPPATCH
|_http-title: Under Construction
| http-webdav-scan:
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, COPY, PROPFIND, SEARCH, LOCK, UNLOCK
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
| WebDAV type: Unknown
| Server Type: Microsoft-IIS/6.0
|_ Server Date: Sat, 26 Aug 2023 20:37:52 GMT
|_http-server-header: Microsoft-IIS/6.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsGranny와 스캔 결과가 너무 동일한 것 같아 찝찝함을 거둘 수 없다..
일단 브라우저로 접속해본다.
오 Granny와 동일한 취약점인가..?
일단 처음본다고 가정하고 gobuster를 진행해본다.
저번 Granny 때 다음엔 다른 wordlist를 써보기로 했었는데 바로 이렇게 기회가 있다니.. 좋구만
하지만 너무 구린 결과가 도출되었다.
$ gobuster dir -w /usr/share/dirbuster/wordlists/directory-list-2.3-small.txt -u http://10.129.95.233/
>
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.95.233/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-small.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Timeout: 10s
===============================================================
2023/08/21 22:24:21 Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 151] [--> http://10.129.95.233/images/]
/Images (Status: 301) [Size: 151] [--> http://10.129.95.233/Images/]
/IMAGES (Status: 301) [Size: 151] [--> http://10.129.95.233/IMAGES/]
/_private (Status: 403) [Size: 1529]나온 것이라고는 private 하나 뿐... frontpage 관련 path는 common.txt가 훨씬 나은 것 같다.
wordlist를 common.txt로 변경하여 다시 gobuster 툴을 돌린다.
$ gobuster dir -u http://10.129.95.233/ -w /usr/share/wordlists/dirb/common.txt
>
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.95.233/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Timeout: 10s
===============================================================
2023/08/21 23:16:28 Starting gobuster in directory enumeration mode
===============================================================
/_private (Status: 403) [Size: 1529]
/_vti_bin (Status: 301) [Size: 157] [--> http://10.129.95.233/%5Fvti%5Fbin/]
/_vti_bin/_vti_adm/admin.dll (Status: 200) [Size: 195]
/_vti_bin/_vti_aut/author.dll (Status: 200) [Size: 195]
/_vti_bin/shtml.dll (Status: 200) [Size: 96]
/_vti_cnf (Status: 403) [Size: 1529]
/_vti_log (Status: 403) [Size: 1529]
/_vti_pvt (Status: 403) [Size: 1529]
/_vti_txt (Status: 403) [Size: 1529]
Progress: 266 / 4615 (5.76%)[ERROR] 2023/08/21 23:16:38 [!] context deadline exceeded (Client.Timeout or context cancellation while reading body)
/aspnet_client (Status: 403) [Size: 218]
/Images (Status: 301) [Size: 151] [--> http://10.129.95.233/Images/]
/images (Status: 301) [Size: 151] [--> http://10.129.95.233/images/]
Progress: 4614 / 4615 (99.98%)
===============================================================
2023/08/21 23:18:55 Finished
===============================================================granny와 동일한 path에서 동일하게 200 OK를 준다.
하지만 이 path는 searchsploit을 했을 때 별다른 취약점이 도출되지 않았었다.

디렉터리리스팅 취약점이 없어서 cadaver 툴도 먹히지 않는다.

davtest 툴을 이용하여 파일업로드가 가능한지 확인해본다.
결과로 봐선 PUT이 아예 되지 않는 것 같다.
$ davtest -url http://10.129.95.233/
>
********************************************************
Testing DAV connection
OPEN SUCCEED: http://10.129.95.233
********************************************************
NOTE Random string for this session: k6K2cHWGcAv
********************************************************
Creating directory
MKCOL FAIL
********************************************************
Sending test files
PUT jhtml FAIL
PUT cgi FAIL
PUT shtml FAIL
PUT pl FAIL
PUT php FAIL
PUT txt FAIL
PUT aspx FAIL
PUT asp FAIL
PUT html FAIL
PUT jsp FAIL
PUT cfm FAIL
********************************************************
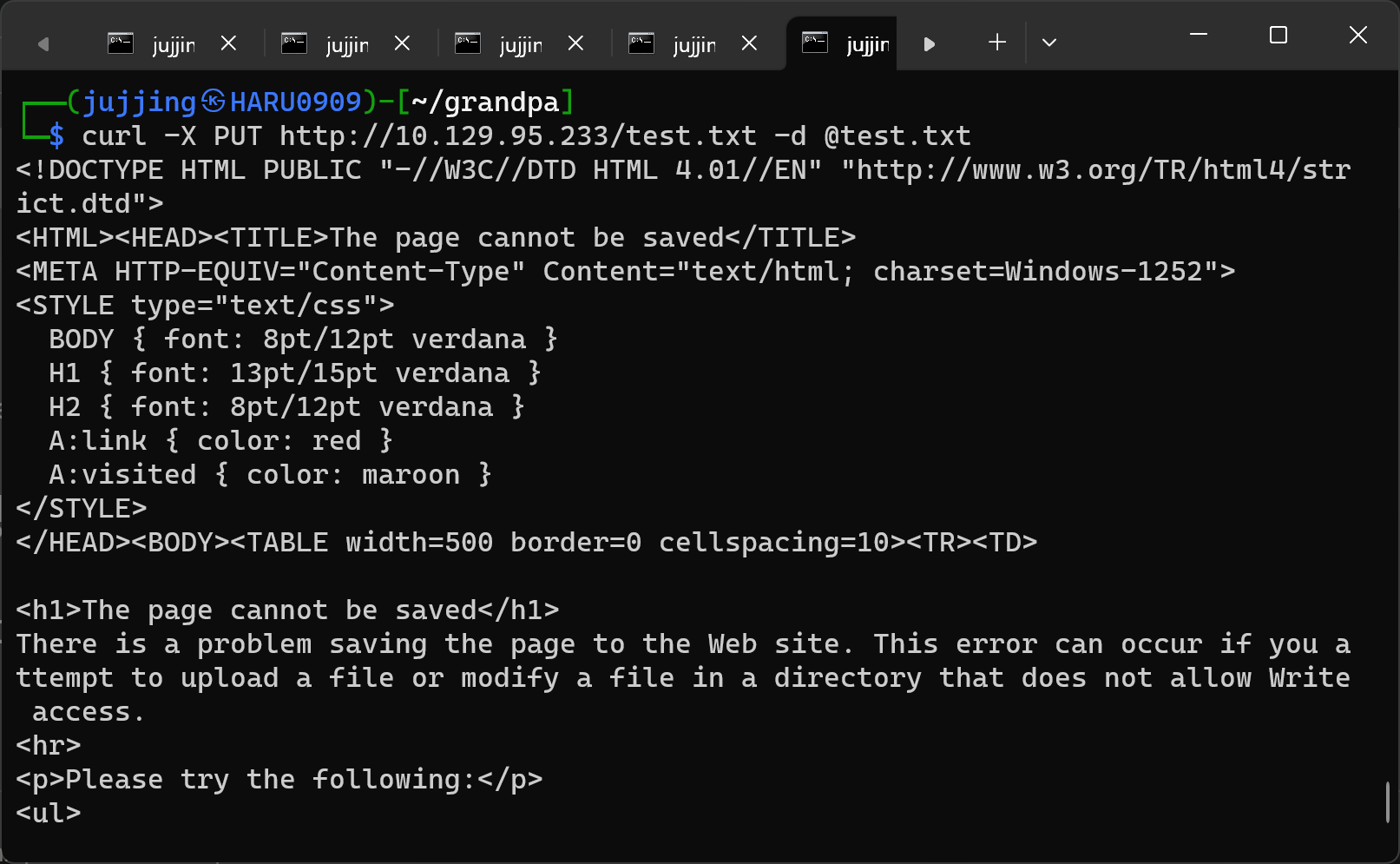
/usr/bin/davtest Summary:curl을 통해 직접 진행해본다.
응답 값을 통해 업로드가 되지 않는 것을 확인할 수 있다.
이외에도 사이트를 좀 돌아다녔으나 서버 응답 헤더에서 노출되는 값 말고는 얻을 수 있는 게 없었다.
경험상 해당 헤더에서 나온 값들은 큰 의미가 없을 것으로 추측된다.

---
별다른 취약한 부분을 찾지 못해서 다시 frontpage 취약점을 찾아야겠다고 마음 먹었다.
아래 툴을 이용하였다.
https://github.com/sensepost/SPartan
┌──(isoEnv)(jujjing㉿HARU0909)-[~/grandpa/SPartan]
└─$ python SPartan.py -u http://10.129.95.233 -f -c
>
██████ ██▓███ ▄▄▄ ██▀███ ▄▄▄█████▓▄▄▄ ███▄ █
▒██ ▒▓██░ ██▒████▄ ▓██ ▒ ██▓ ██▒ ▓▒████▄ ██ ▀█ █
░ ▓██▄ ▓██░ ██▓▒██ ▀█▄ ▓██ ░▄█ ▒ ▓██░ ▒▒██ ▀█▄ ▓██ ▀█ ██▒
▒ ██▒██▄█▓▒ ░██▄▄▄▄██▒██▀▀█▄ ░ ▓██▓ ░░██▄▄▄▄██▓██▒ ▐▌██▒
▒██████▒▒██▒ ░ ░▓█ ▓██░██▓ ▒██▒ ▒██▒ ░ ▓█ ▓██▒██░ ▓██░
▒ ▒▓▒ ▒ ▒▓▒░ ░ ░▒▒ ▓▒█░ ▒▓ ░▒▓░ ▒ ░░ ▒▒ ▓▒█░ ▒░ ▒ ▒
░ ░▒ ░ ░▒ ░ ▒ ▒▒ ░ ░▒ ░ ▒░ ░ ▒ ▒▒ ░ ░░ ░ ▒░
░ ░ ░ ░░ ░ ▒ ░░ ░ ░ ░ ▒ ░ ░ ░
░ ░ ░ ░ ░ ░ ░
Sharepoint & Frontpage Scanner
-----------------------------------------------------------------------------
[+] Initiating Frontpage fingerprinting...
[+] [1][200][195b] - http://10.129.95.233/_vti_bin/_vti_aut/author.exe
[+] Frontpage for Linux found
[+] [2][200][195b] - http://10.129.95.233/_vti_bin/_vti_aut/author.dll
[+] Frontpage for Windows found
[+] [3][200][1754b] - http://10.129.95.233/_vti_inf.html
[+] Frontpage config:
<html>
<head>
<meta http-equiv="Content-Type"
content="text/html; charset=iso-8859-1">
<title> FrontPage Configuration Information </title>
</head>
<body>
<!-- _vti_inf.html version 0.100>
<!--
This file contains important information used by the FrontPage client
(the FrontPage Explorer and FrontPage Editor) to communicate with the
FrontPage server extensions installed on this web server.
The values below are automatically set by FrontPage at installation. Normally, you do not need to modify these values, but in case
you do, the parameters are as follows:
'FPShtmlScriptUrl', 'FPAuthorScriptUrl', and 'FPAdminScriptUrl' specify
the relative urls for the scripts that FrontPage uses for remote
authoring. These values should not be changed.
'FPVersion' identifies the version of the FrontPage Server Extensions
installed, and should not be changed.
--><!-- FrontPage Configuration Information
FPVersion="5.0.2.6790"
FPShtmlScriptUrl="_vti_bin/shtml.dll/_vti_rpc"
FPAuthorScriptUrl="_vti_bin/_vti_aut/author.dll"
FPAdminScriptUrl="_vti_bin/_vti_adm/admin.dll"
TPScriptUrl="_vti_bin/owssvr.dll"
-->
<p><!--webbot bot="PurpleText"
preview="This page is placed into the root directory of your FrontPage web when FrontPage is installed. It contains information used by the FrontPage client to communicate with the FrontPage server extensions installed on this web server. You should not delete this file."
--></p>
<h1>FrontPage Configuration Information </h1>
<p>In the HTML comments, this page contains configuration
information that the FrontPage Explorer and FrontPage Editor need to
communicate with the FrontPage server extensions installed on
this web server. Do not delete this page.</p>
</body>
</html>
-----------------------------------------------------------------------------
[+] Initiating Frontpage pvt scan...
-----------------------------------------------------------------------------
[+] Initiating Frontpage bin scan...
[+] [23][200][1754b] - http://10.129.95.233/_vti_inf.html
[+] [24][200][195b] - http://10.129.95.233/_vti_bin/shtml.dll/_vti_rpc
[+] [26][200][195b] - http://10.129.95.233/_vti_bin/_vti_adm/admin.dll
[+] [27][200][195b] - http://10.129.95.233/_vti_bin/_vti_adm/admin.exe
[+] [28][200][195b] - http://10.129.95.233/_vti_bin/_vti_aut/author.exe
[+] [31][200][195b] - http://10.129.95.233/_vti_bin/shtml.exe/_vti_rpc
[+] [32][200][195b] - http://10.129.95.233/_vti_bin/_vti_aut/author.dll
-----------------------------------------------------------------------------확실히 gobuster를 돌린 것보다 많은 정보를 확인할수 있다..
_vti_rpc가 취약 포인트라고 알려져 있는데 해당 정보를 찾아보면 될 것 같다.
https://github.com/deepak0401/Front-Page-Exploit
위 링크를 토대로 요청을 보내보니 서버 버전 정보가 노출되긴 하였다만 별 필요없는 정보였다.
user 정보는 나오는 데이터가 없었다.
GitHub - deepak0401/Front-Page-Exploit: HTTP requests of FrontPage expolit
HTTP requests of FrontPage expolit. Contribute to deepak0401/Front-Page-Exploit development by creating an account on GitHub.
github.com


-----------
다시 OS 정보(IIS 6.0)로 공격을 시도해본다.

WebDAV 'ScStoragePathFromUrl' Remote Buffer Overflow를 이용한다.

CVE-2017-7269 exploit을 이용하였으나 에러가 나서 일단 여기서 마무리